This content originally appeared on HackerNoon and was authored by Techbeat
How are you, hacker?
 Want to know what’s trending right now?:
The Techbeat by HackerNoon has got you covered with fresh content from our trending stories of the day! Set email preference here.
## Selective Privacy: How BelNet’s Split Tunneling Balances Speed and Security
Want to know what’s trending right now?:
The Techbeat by HackerNoon has got you covered with fresh content from our trending stories of the day! Set email preference here.
## Selective Privacy: How BelNet’s Split Tunneling Balances Speed and Security 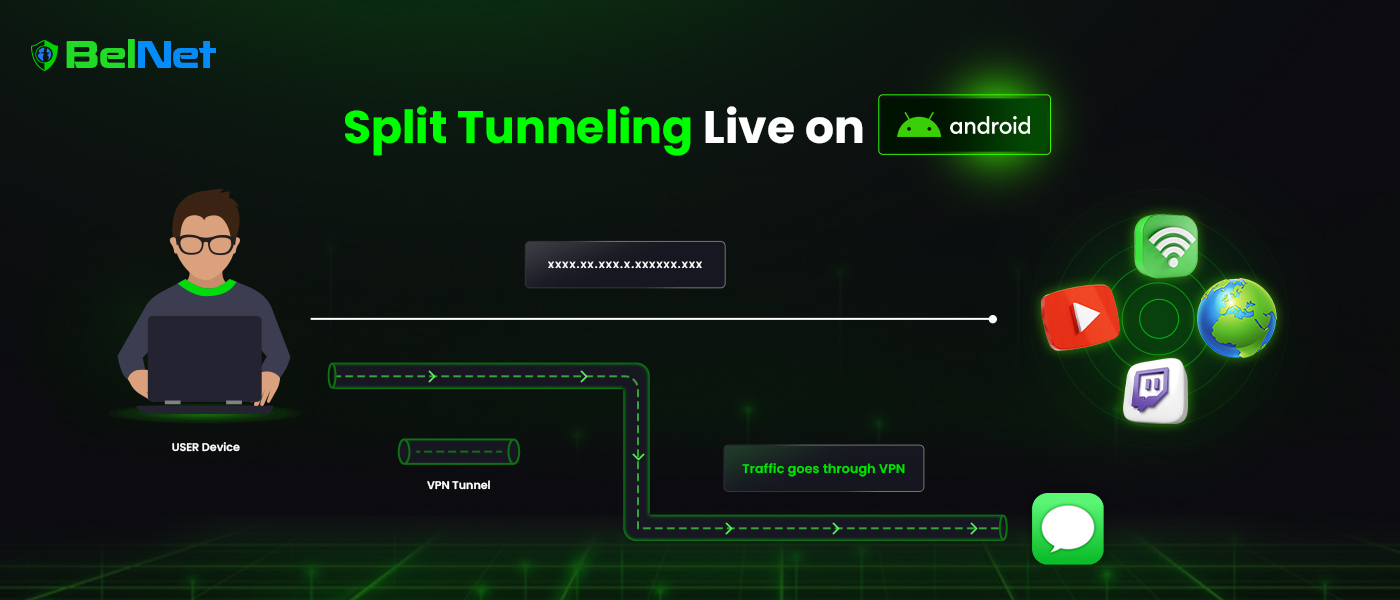 By @beldexcoin [ 4 Min read ]
BelNet introduces split tunneling for faster, more private browsing—select which data is encrypted, and enjoy speed without compromising confidentiality. Read More.
By @beldexcoin [ 4 Min read ]
BelNet introduces split tunneling for faster, more private browsing—select which data is encrypted, and enjoy speed without compromising confidentiality. Read More.
**[Mac.c Stealer Takes on AMOS:
A New Rival Shakes Up the macOS Infostealer Market](https://hackernoon.com/macc-stealer-takes-on-amos-a-new-rival-shakes-up-the-macos-infostealer-market)**  By @moonlock [ 8 Min read ]
Moonlock analysed Mac.c stealer, a new rival to AMOS. Learn its tactics, code reuse, and “building in public” strategy. Read More.
By @moonlock [ 8 Min read ]
Moonlock analysed Mac.c stealer, a new rival to AMOS. Learn its tactics, code reuse, and “building in public” strategy. Read More.
Turn a Regular Wallet into a Smart Account with EIP 7702 
By @hacker39947670 [ 13 Min read ] Learn how EIP-7702 enables smart wallet features for existing Ethereum accounts. Complete developer guide with code examples. Read More.
Why Developers Need Mobile-First Error Tracking (And How We Built It) 
By @danzabrotski [ 7 Min read ] Mobile-first app monitoring that frees developers from desktop-bound error tracking. Real-time phone notifications, AI integration roadmap, and startup benefits Read More.
Here’s The Exact Indie-Hacking Vibe-Coding Setup I Use as a Middle-Aged Product Manager 
By @ivankuznetsov [ 7 Min read ] Middle-aged PM shares his AI-powered vibe-coding setup after restarting dev journey to beat burnout. Read More.
Meta’s AI Boss Just Called LLMs ‘Simplistic’ — Here’s What He’s Building Instead 
By @hacker-Antho [ 8 Min read ] Yann LeCun, Chief AI Scientist at Meta, discusses the future of AI. Read More.
Immutable Backups: Everything You Need To Know To Protect Your Cloud 
By @n2w [ 6 Min read ] Learn how immutable backups prevent ransomware, ensure data integrity, and meet compliance needs with secure, tamper-proof cloud data protection. Read More.
Europe’s Data Vision: Dataspaces for Zero-Trust AI Infrastructure 
By @khamisihamisi [ 6 Min read ] This case study explores a pioneering Huberta project that embraces zero-trust architecture, metadata-first orchestration, and mathematical compliance via PDEs. Read More.
Dogecoin Price Prediction: Can It Hit $10 Or Will Pepeto Take The Lead? 
By @btcwire [ 3 Min read ] Dogecoin aims for $10 as altseason gains momentum, but Pepeto is winning over early investors with real infrastructure, community traction, and major upside. Read More.
How I Set Up a Cowrie Honeypot to Capture Real SSH Attacks 
By @authenticpeach [ 10 Min read ] Simulate real-world SSH attacks with Cowrie, log attacker behavior, and analyze tactics using MITRE ATT&CK in this hands-on honeypot project. Read More.
Toward Holistic Evaluation of LLMs: Integrating Human Feedback with Traditional Metrics 
By @nileshbh [ 16 Min read ] A deep dive into why LLMs need both metrics and human feedback for real-world accuracy, ethics, and performance. Read More.
Mobile AI with ONNX Runtime: How to Build Real-Time Noise Suppression That Works 
By @sergeyd [ 13 Min read ] Build real-time AI noise suppression for Android with ONNX Runtime. Complete tutorial with working code, performance tips, and 70% APK size reduction. Read More.
Why Morpho’s $9B Network Is Powering Lending on Pharos’ RWA Blockchain 
By @ishanpandey [ 3 Min read ] Pharos teams up with Morpho to launch native, modular lending infrastructure for real-world asset markets on-chain. Read More.
Ants and Algorithms: 5 Solutions Inspired From Insects 
By @erickayscifi [ 6 Min read ] Discover how ants inspire tech technology. Explore ACO, swarm intelligence, biomimicry, and insect cyberware in this fascinating article. Read More.
Data Privacy Challenges in Open MCP Architectures 
By @mayankc [ 29 Min read ] MCP lets AI access tools in real time—but also expands risks. This guide explores its security pitfalls and best practices for safe deployment. Read More.
YOLO Jungle: С3, C2F, C3K2 — What Do They Even Mean? 
By @epleteneva [ 11 Min read ] How modern YOLO architectures — including C3, C2f, C3K, and C3K2 blocks — build on the Cross-Stage Partial (CSP) concept to boost efficiency. Read More.
How McKinsey Rebuilt Its Business Around AI—And Why It’s Working 
By @hacker68060072 [ 4 Min read ] Discover how McKinsey integrated AI into their operations to drive efficiency, collaboration, and real business value. Learn from their approach. Read More.
Why is Upwork Splitting Into Two Companies? 
By @nebojsaneshatodorovic [ 3 Min read ] Upwork is splitting into two by making the enterprise business a stand-alone entity. Read More.
Our Communication No Longer Belongs to Us 
By @bolshiyanov [ 3 Min read ] AI could help you create your own private contact room on WhatsApp 1.0. Read More.
Why No Transaction Fee Mechanism Can Truly Be Collusion-Proof 
By @escholar [ 5 Min read ]
Your cheat sheet to understanding incentive-compatibility in transaction fee mechanisms—UIC, MIC, SCP, and the limits of truthfulness. Read More.
 What happened in your world this week? It’s been said that writing can help consolidate technical knowledge, establish credibility, and contribute to emerging community standards. Feeling stuck? We got you covered
What happened in your world this week? It’s been said that writing can help consolidate technical knowledge, establish credibility, and contribute to emerging community standards. Feeling stuck? We got you covered 

 ANSWER THESE GREATEST INTERVIEW QUESTIONS OF ALL TIME
We hope you enjoy this worth of free reading material. Feel free to forward this email to a nerdy friend who’ll love you for it.
See you on Planet Internet! With love,
The HackerNoon Team
ANSWER THESE GREATEST INTERVIEW QUESTIONS OF ALL TIME
We hope you enjoy this worth of free reading material. Feel free to forward this email to a nerdy friend who’ll love you for it.
See you on Planet Internet! With love,
The HackerNoon Team 
.gif)
This content originally appeared on HackerNoon and was authored by Techbeat