This content originally appeared on HackerNoon and was authored by Web Fonts
Table of Links
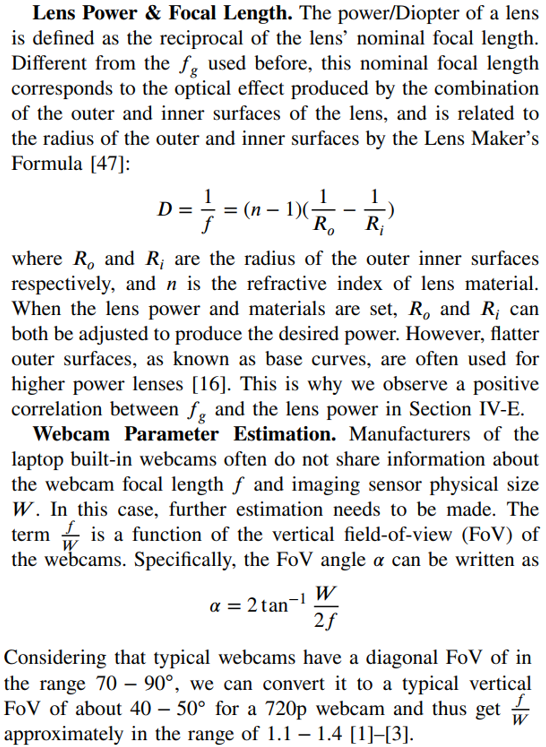
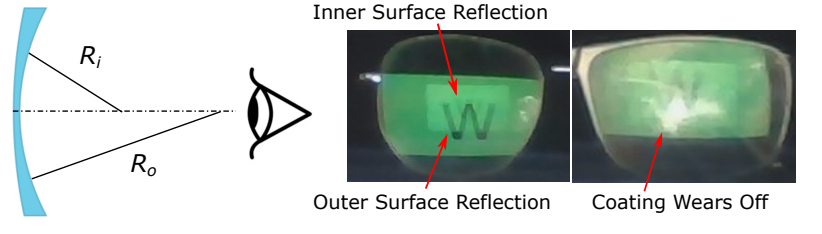
III. Webcam Peeking through Glasses
IV. Reflection Recognizability & Factors
V. Cyberspace Textual Target Susceptibility
IX. Conclusion, Acknowledgment, and References
APPENDIX A: Equipment Information
APPENDIX B: Viewing Angle Model
APPENDIX C: Video Conferencing Platform Behaviors
APPENDIX D: Distortion Analysis
APPENDIX E: Web Textual Targets
APPENDIX A EQUIPMENT INFORMATION
\
\ Lab Setting Experiment Equipment. The Acer laptop [7] has a screen width of 38 cm and height of 190 mm and a 720p built-in webcam. The OS is Ubuntu 20.04. The OS and browser zoom ratios are default (100%). All the photos and videos are collected with the Cheese [13] webcam application. The photos are in PNG format and the videos are in WEBM format. The Samsung laptop used as the attacker device has OS Windows 10 Pro. The recordings are collected with OBS Studio in MP4 format.
\

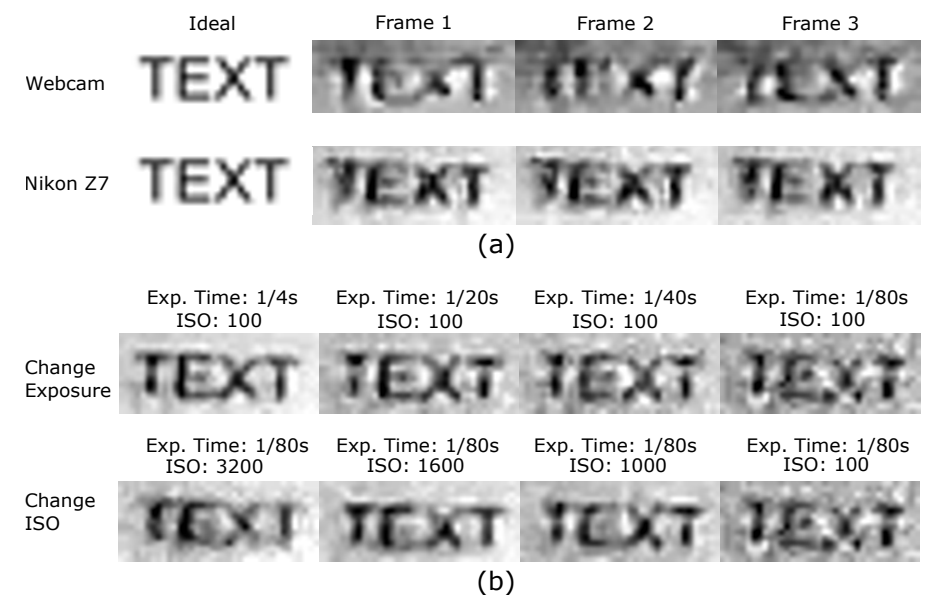
\ Nikon Z7: The photos are in JPEG format (highest quality) and the videos are in MP4 format. We compared these formats with the compression-less (raw) photo and video formats provided by Nikon Z7 but didn’t find an obvious difference in the image quality.
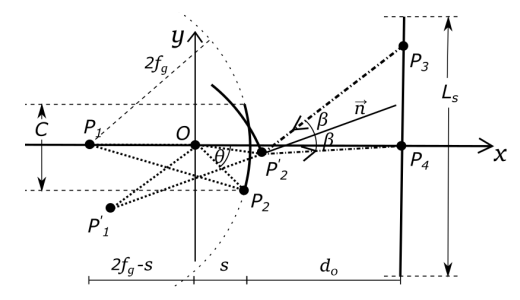
APPENDIX B VIEWING ANGLE MODEL
\
\
\
\
\
\
\
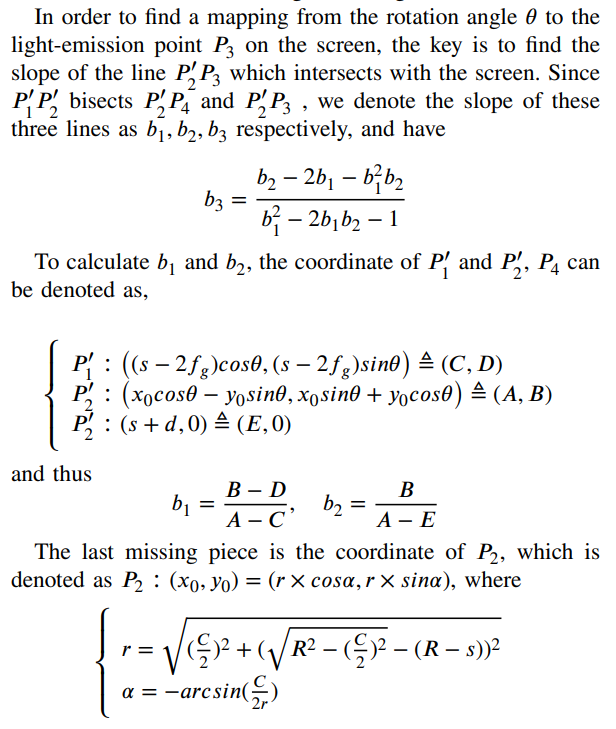
\ \ We note that the measured ranges in Table II are uniformly larger than the theoretical values, which could be caused by a coarse estimation of the distance s since the actual distance between the lens and the rotation center is hard to determine, and the fact that the model approximates the camera as a point instead of a surface.
APPENDIX C VIDEO CONFERENCING PLATFORM BEHAVIORS
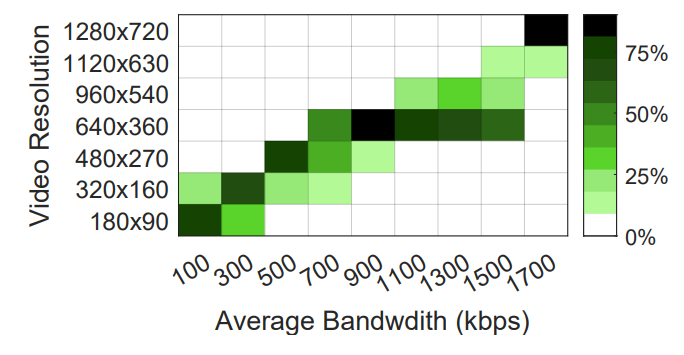
Zoom Under Low Bandwidths. When network bandwidth got smaller than 4 Mbps, we found Zoom will first experience a short period of aggravated packet loss, and then rapidly decrease the video resolution to compensate for it. Video resolution will soon be increased again by sacrificing frame
\
\
\
\
\
\ \ rate as well as compression loss. Zoom will still try to recover high frame rates later by further increasing the video compression loss. Through our experiments, we noticed that when the bandwidth was larger than 1500 kbps, Zoom was able to maintain a 1280*720 resolution with a frame rate very close to 30 fps. We observed lower resolutions when the bandwidth is lower than 1500 kbps, as shown in Figure 13. Skype and Google Meet do not provide statistics like resolution, frame rate, and bandwidth. But our visual inspection suggests they take a similar approach as Zoom to handle bandwidth issues.
\ Video Quality Control. Currently, Zoom and Skype do not provide an option for users to control video resolution or quality directly. Google Meet only allows users to switch between 720p and 360p send and receive video resolutions. However, users can limit their system or process bandwidths using software like NetLimiter to decrease video quality even without the conferencing platform offering such an option.
\
:::info Authors:
(1) Yan Long, Electrical Engineering and Computer Science, University of Michigan, Ann Arbor, USA (yanlong@umich.edu);
(2) Chen Yan, College of Electrical Engineering, Zhejiang University, Hangzhou, China (yanchen@zju.edu.cn);
(3) Shilin Xiao, College of Electrical Engineering, Zhejiang University, Hangzhou, China (xshilin@zju.edu.cn);
(4) Shivan Prasad, Electrical Engineering and Computer Science, University of Michigan, Ann Arbor, USA (shprasad@umich.edu);
(5) Wenyuan Xu, College of Electrical Engineering, Zhejiang University, Hangzhou, China (wyxu@zju.edu.cn);
(6) Kevin Fu, Electrical Engineering and Computer Science, University of Michigan, Ann Arbor, USA (kevinfu@umich.edu).
:::
:::info This paper is available on arxiv under ATTRIBUTION-NONCOMMERCIAL-NODERIVS 4.0 INTERNATIONAL license.
:::
\
This content originally appeared on HackerNoon and was authored by Web Fonts