This content originally appeared on DEV Community and was authored by Anil Kumar
 Today, let’s explore the key differences between 𝑲𝒖𝒃𝒆𝒓𝒏𝒆𝒕𝒆𝒔 𝑪𝒐𝒏𝒇𝒊𝒈𝑴𝒂𝒑𝒔 & 𝑺𝒆𝒄𝒓𝒆𝒕𝒔!
Today, let’s explore the key differences between 𝑲𝒖𝒃𝒆𝒓𝒏𝒆𝒕𝒆𝒔 𝑪𝒐𝒏𝒇𝒊𝒈𝑴𝒂𝒑𝒔 & 𝑺𝒆𝒄𝒓𝒆𝒕𝒔! 
When it comes to 𝒂𝒑𝒑𝒍𝒊𝒄𝒂𝒕𝒊𝒐𝒏 𝒔𝒆𝒄𝒖𝒓𝒊𝒕𝒚, everyone agrees on its importance. One best practice is to separate configuration data, such as user IDs, passwords, or other sensitive information, from the application code. But how can we achieve this? That’s where ConfigMaps and Secrets come into play!
Understanding ConfigMaps vs. Secrets
𝑪𝒐𝒏𝒇𝒊𝒈𝑴𝒂𝒑𝒔:
A Kubernetes object for storing non-confidential configuration data (e.g., config files, URLs) as key-value pairs.
Characteristics:
1⃣ Stored in plain text.
2⃣ Allows configuring applications without modifying container images.
3⃣ No built-in encryption.
Pros:
 Separates configuration data from application code.
Separates configuration data from application code.
 Enables dynamic updates without rebuilding images or restarting applications.
Enables dynamic updates without rebuilding images or restarting applications.
 Supports multiple key-value pairs.
Supports multiple key-value pairs.
Cons:
 Not suitable for sensitive data.
Not suitable for sensitive data.
 Requires careful management to avoid outdated or inconsistent data.
Requires careful management to avoid outdated or inconsistent data.
Use Cases:
1) Environment variables.
2) Application settings.
3) External service URLs.
How to Create ConfigMaps (attached in picture format) :
- From literals (command line).
- From files: a) As environment variables. b) As mounted volumes. ———————— 𝑺𝒆𝒄𝒓𝒆𝒕𝒔:
A Kubernetes object designed to store sensitive data such as passwords, API keys, or tokens securely.
Characteristics:
1⃣ Stored as Base64-encoded strings.
2⃣ Used to pass sensitive data securely to applications.
3⃣ Supports encryption at rest (when API server encryption is enabled).
Pros:
 Enhances security by managing sensitive data separately.
Enhances security by managing sensitive data separately.
 Provides fine-grained access control using RBAC.
Provides fine-grained access control using RBAC.
 Supports integration with external secret management tools (e.g., HashiCorp Vault).
Supports integration with external secret management tools (e.g., HashiCorp Vault).
Cons:
 Base64 encoding is not true encryption and requires additional measures.
Base64 encoding is not true encryption and requires additional measures.
 May require external tools for optimal security practices (e.g., encryption at rest).
May require external tools for optimal security practices (e.g., encryption at rest).
Use Cases:
1) Database credentials.
2) OAuth tokens.
3) SSL/TLS certificates.
How to Create Secrets( attached in picture format):
- From literals (command line).
- From files:
a) As environment variables.
b) As mounted volumes.
————————
Key Notes
 :
:
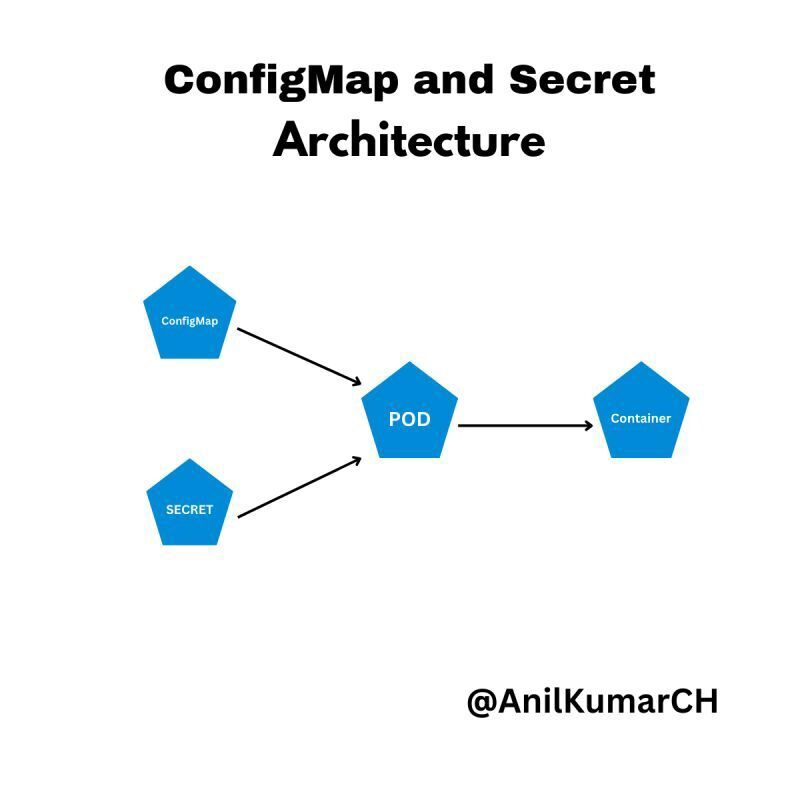
1⃣ 𝑩𝒆𝒇𝒐𝒓𝒆 𝑼𝒔𝒆: ConfigMaps and Secrets must be created first before they can be used in a Pod.
2⃣ 𝑴𝒐𝒖𝒏𝒕𝒊𝒏𝒈:
1) Both can be mounted as volumes.
2) Ensure they are first mounted into the Pod as “volumes” before attaching them to containers as “volumeMounts” to avoid errors.
3⃣ 𝑺𝒆𝒄𝒖𝒓𝒊𝒕𝒚 𝑻𝒊𝒑:
Secrets are Base64-encoded, not encrypted by default. For enhanced security, enable encryption at rest or use external tools.
 Comment your thoughts below! Let’s discuss more about Kubernetes and its powerful features.
Comment your thoughts below! Let’s discuss more about Kubernetes and its powerful features.
Follow Anil kumar  for more content like this!
for more content like this!
This content originally appeared on DEV Community and was authored by Anil Kumar


 !
!